One Afternoon, Lasting Impact

It's unlikely that I'll add any later projects of this simplicity, but due to its incredible practicality, my key companion has earned a spot on this page.
Beyond the challenge of an afternoon build, this project was designed to solve two problems I was facing:
- When walking from one uni building to another, I would need to grab my wallet from my bag so I can use my student card as a key fob. This only took about 15 seconds but would happen five to six times every day.
- A traditional keyring prevented me from using that trouser pocket for anything else unless I didn't mind it getting scratched by the keys' edges.



The simple solution I came up with resembles a Swiss Army Knife to contain all the rough angles, as well as featuring an RFID tag with the information held on my student card.
This allows me to access all areas I would usually be able to with my student ID as well as make transactions around campus.
I first took the necessary dimensions to draw up some simple blanks of my keys in CAD.
All I need is the outer perimeter and hole placement so I can play around until I find an assembly I like the look of.
All I need is the outer perimeter and hole placement so I can play around until I find an assembly I like the look of.


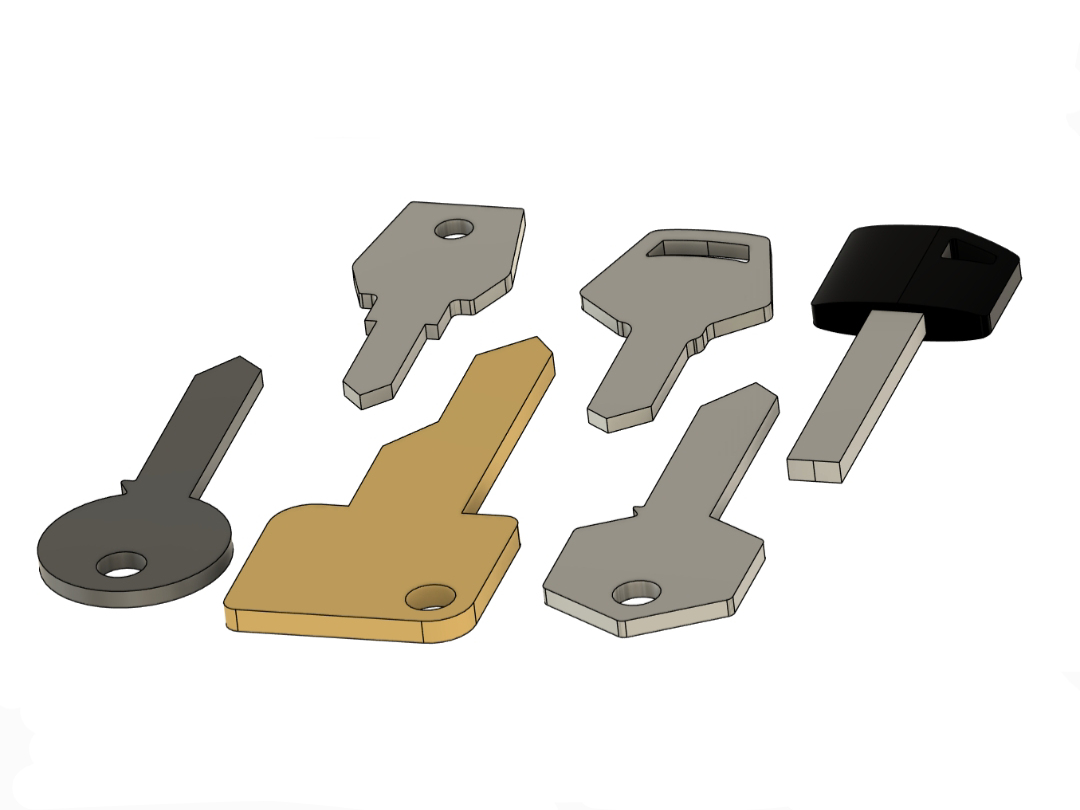
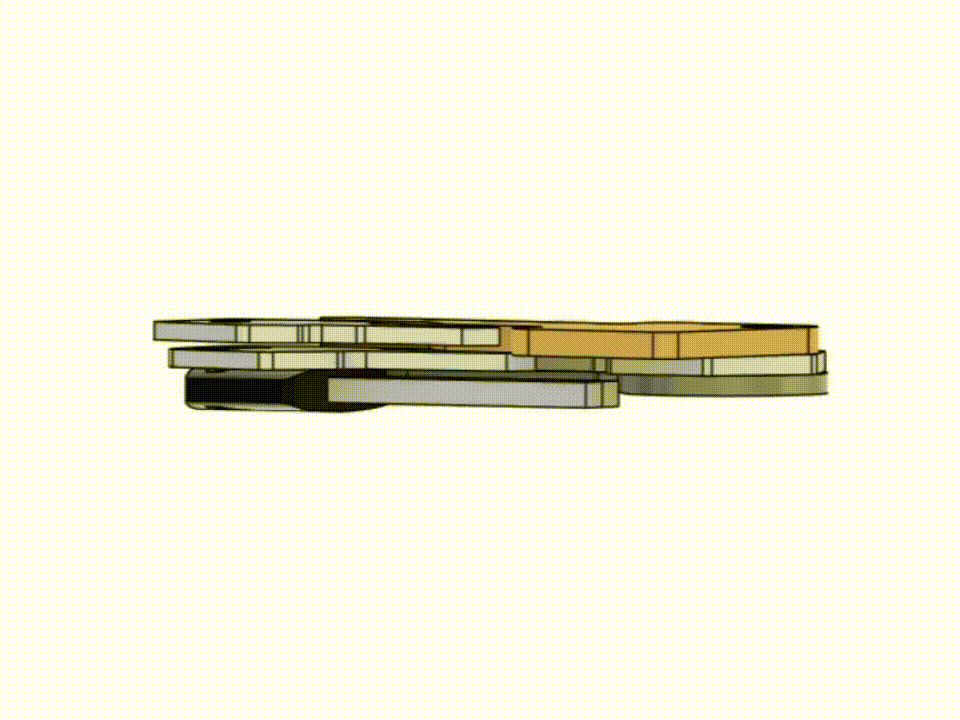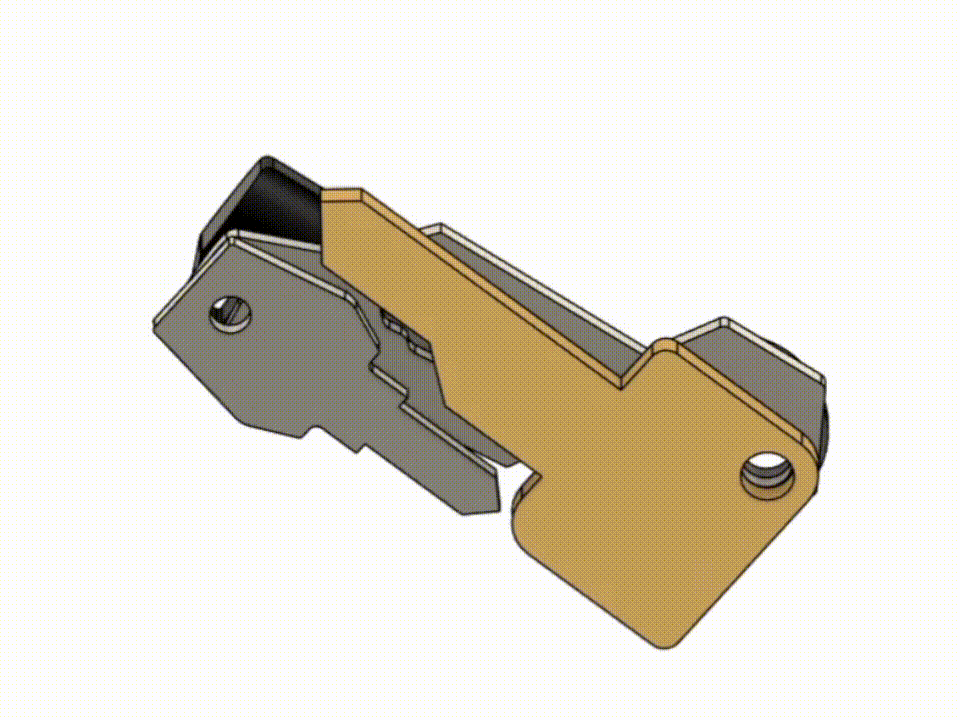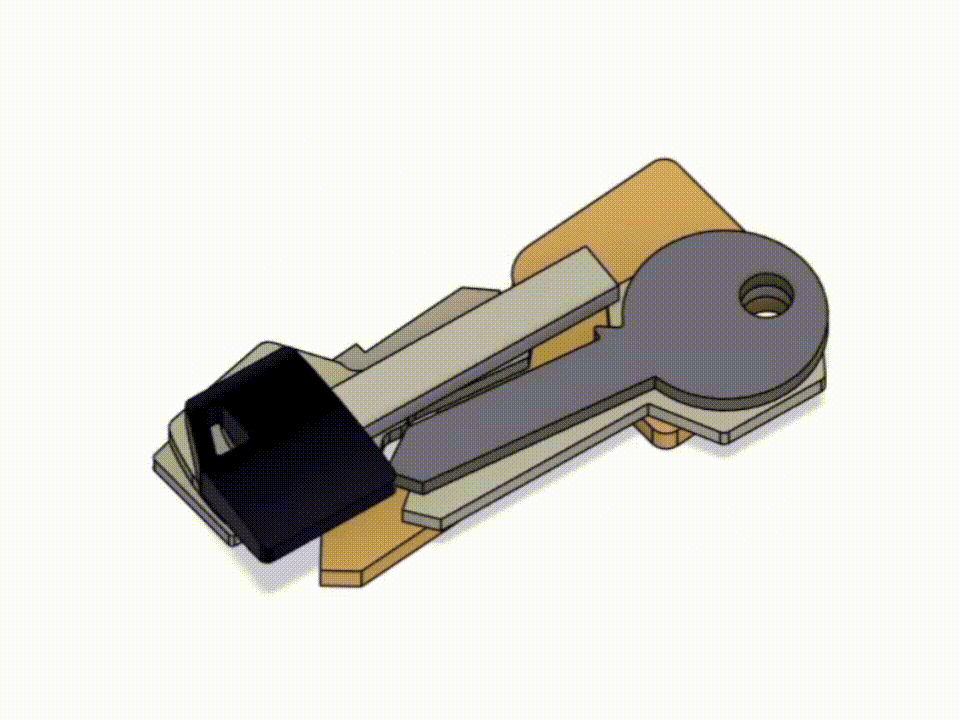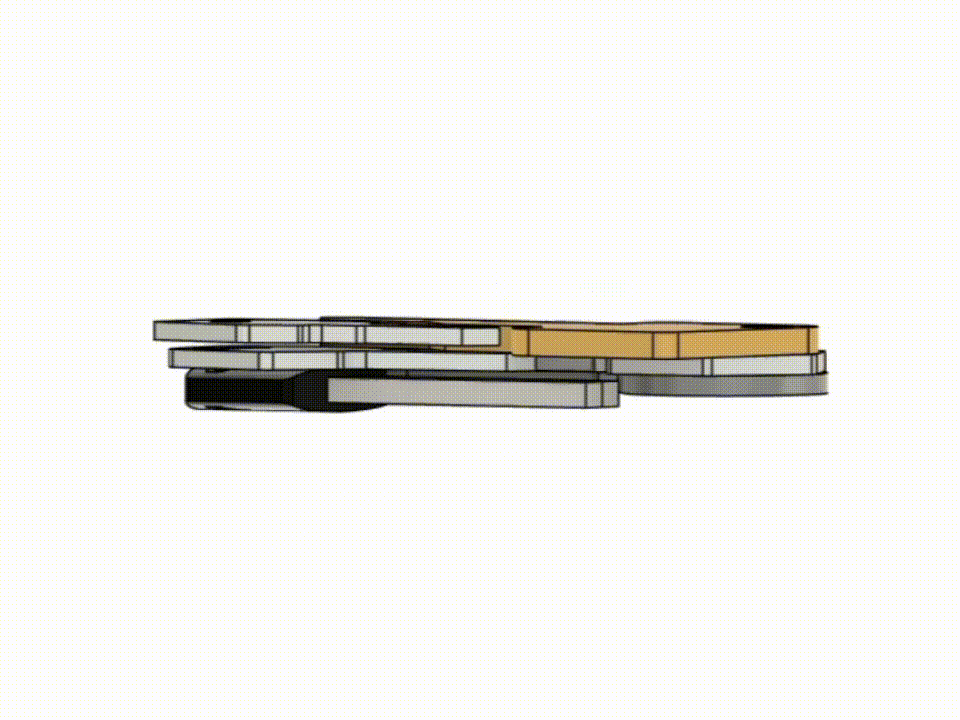
The front and back plates were designed in Autodesk Fusion 360.
The shape took some tweaking to look right since some of the keys don't have their hole in the center of the head.
At the time of making this, our workshop had just received its first Bambu Lab X1C with an AMS module allowing for multimaterial printing.
I decided this small project would make a great first test of the multicolour capabilities. I'll explain the significance of the symbols later on.
The plates are held together with M3 screws and a couple of self locking nuts that fit snugly into the bottom plate.
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
Both halves printed side by side in less than an hour.
Considering the difference in tone between both filaments, I'm really impressed at the lack of impurity in the lighter areas and how clean the seams are.
The bottom plate also came out flawlessly, with the nuts firmly held after being persuaded gently with a mallet.




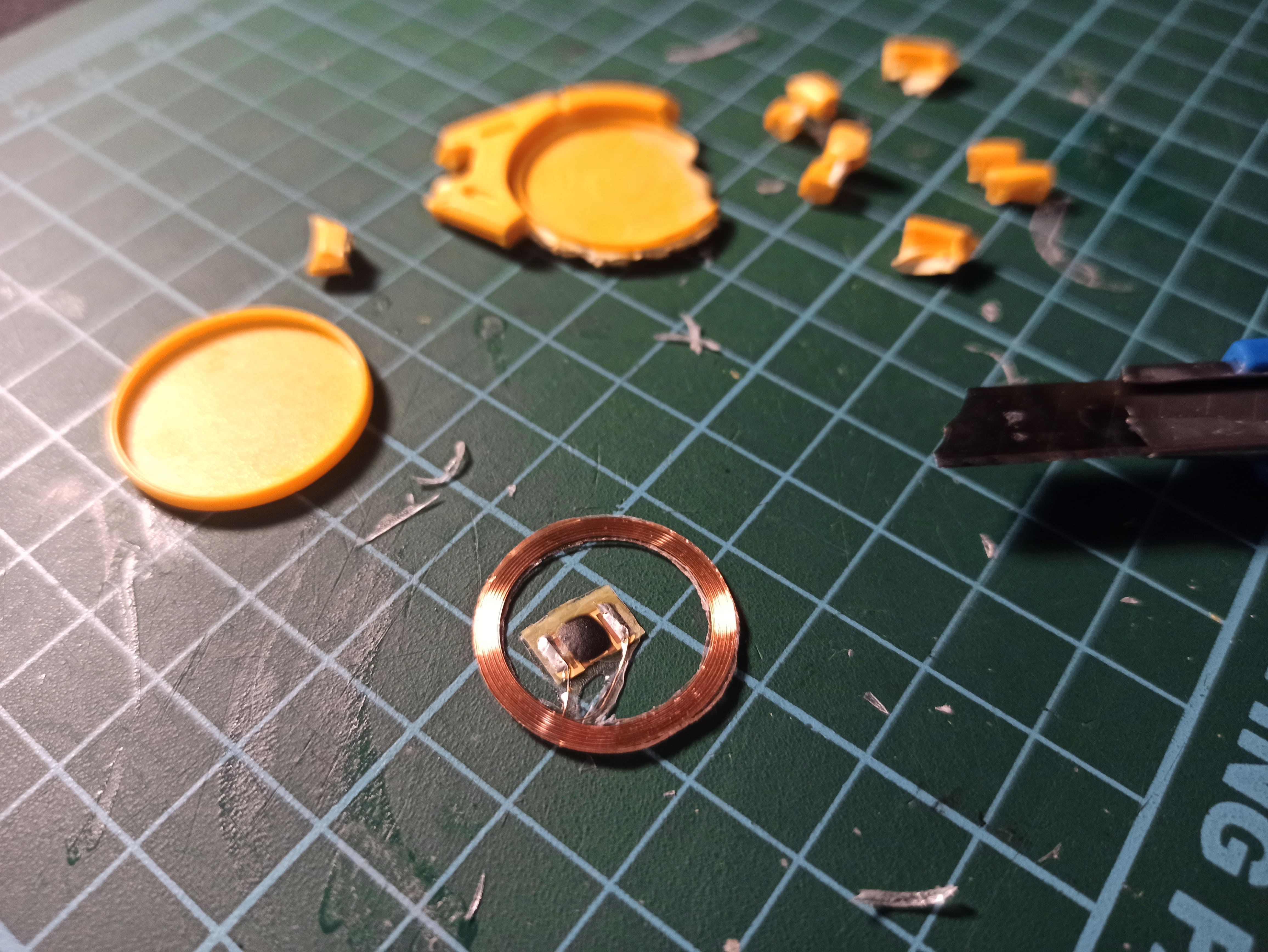
The RFID chip came from a cheap AliExpress 13.56MHz key fob with writable sector 0 capabilities (I'll get back to this later)
There's nothing notable about the assembly.
I had to shorten the screws for them to end up flush agaist the nuts, superglue the chip in it's compartment and top it off with a small disk cut from a 1.5mm plexiglass sheet (visible in the 4th picture below).
Thankfully it's flexible enough to be cut with scissors at this thickness.


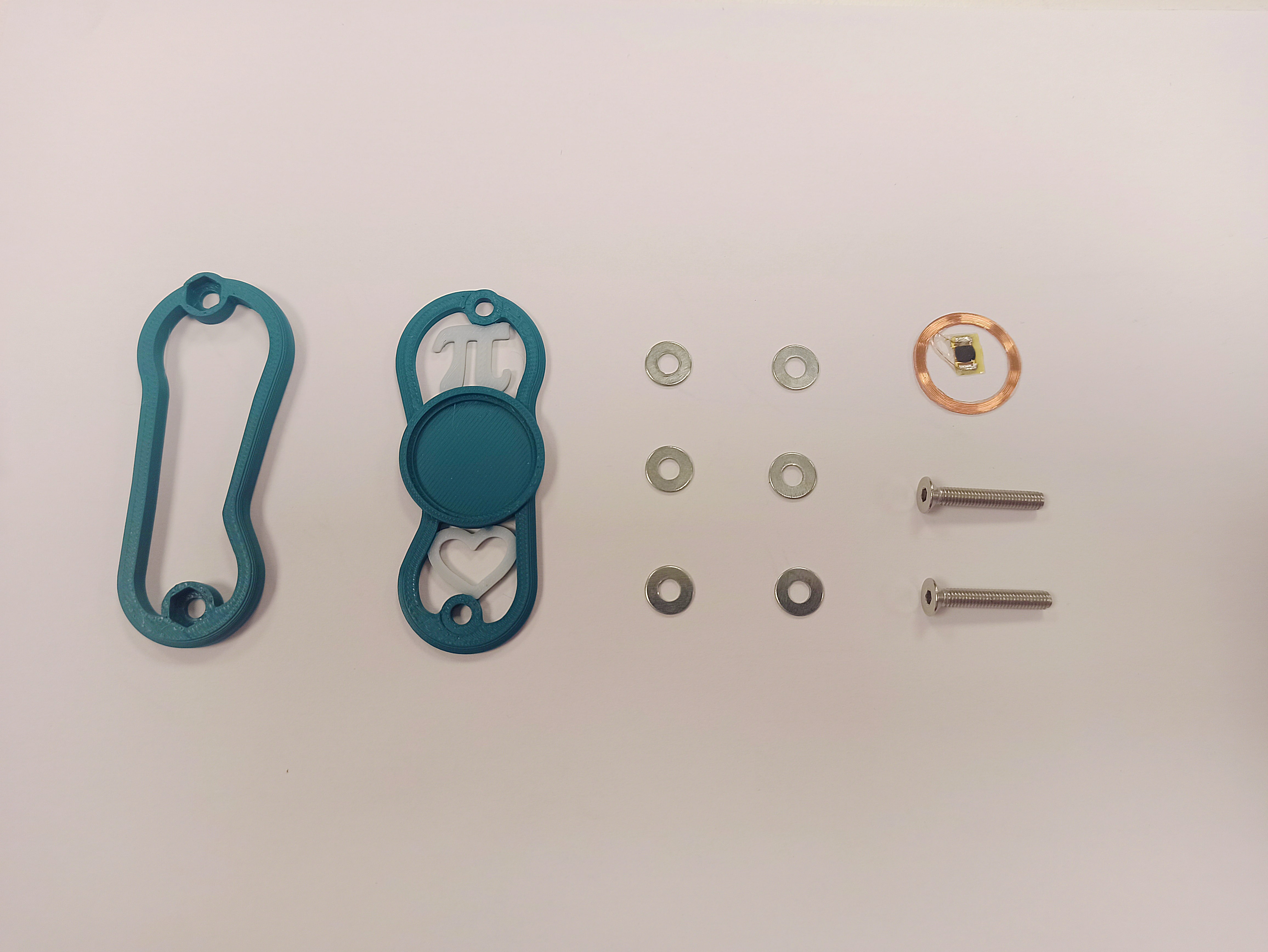

There we go, that's the hardware done! Took a little over 2 and a half hours.
I'd like to add a disclaimer here to say I understand the risks of showing the key cuts on some of these photos.
Most of the keys no longer present a security risk due to me having changed address since taking these.
If you look closely however, you'll see that some (which I still use) have been carefully removed.
The π and ♡ symbols make up my nickname given to me in first year.
"Pi Cœur" in french sounds like "Picker": a reference to both my lock picking hobby and being a Brit. Neat right?

All that remains is to copy the authentication data from my ID to the chip in the front plate.
This is only possible because of a couple of factors. For an engineering university with a good reputation, the security measures are a little disappointing:
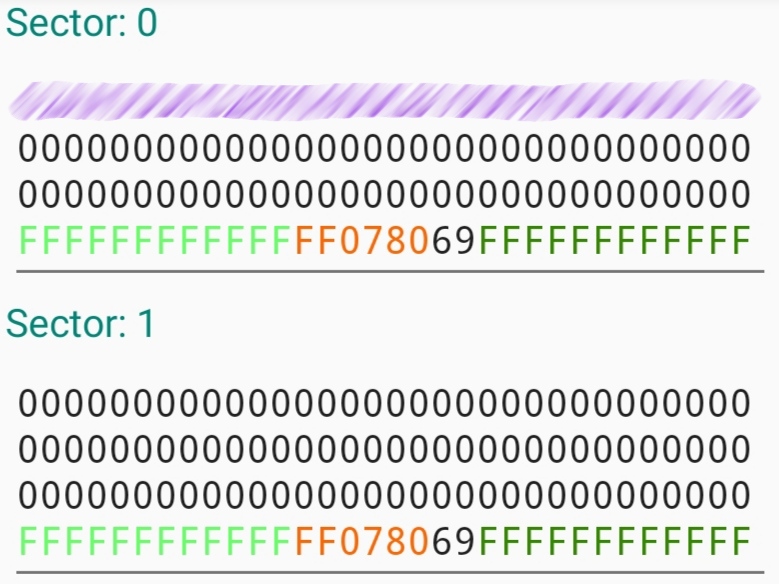
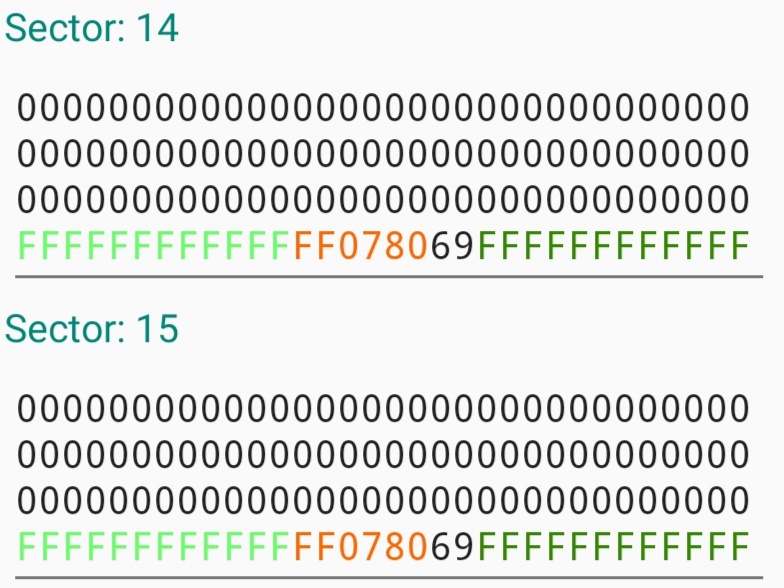
Of the 16 sectors where data can be stored in hexadecimal on the cards, only 15 are writable, with the first one—Sector 0—being a fixed, read-only manufacturer section containing the Unique Identifier (UID). This sector is the only one containing data on my ID, which will be somehow linked to my profile in a database somewhere and relies on the card being unique as sole security measure. Or at least that's the theory, AliExpress offers a wide choice of tags that allow for this section to be written to. The easiest way to do this is with a phone app such as MIFARE that uses the nfc coil in the back of a phone to read and write to chips. One way of increasing the security for the establishment is to use a rolling code algorithm in which the card data is updated every time it is scanned and can also be prevented from being read by some readers. Instead of checking the data agaist a fixed key, the information on the card must respect certain criteria after being subject to binary operations and masks.
I assume this is what my university is switching to because new student's cards no longer work the same way and can't be copied using MIFARE.
Of the 16 sectors where data can be stored in hexadecimal on the cards, only 15 are writable, with the first one—Sector 0—being a fixed, read-only manufacturer section containing the Unique Identifier (UID). This sector is the only one containing data on my ID, which will be somehow linked to my profile in a database somewhere and relies on the card being unique as sole security measure. Or at least that's the theory, AliExpress offers a wide choice of tags that allow for this section to be written to. The easiest way to do this is with a phone app such as MIFARE that uses the nfc coil in the back of a phone to read and write to chips. One way of increasing the security for the establishment is to use a rolling code algorithm in which the card data is updated every time it is scanned and can also be prevented from being read by some readers. Instead of checking the data agaist a fixed key, the information on the card must respect certain criteria after being subject to binary operations and masks.
I assume this is what my university is switching to because new student's cards no longer work the same way and can't be copied using MIFARE.

Please consider the ethics and legality of any projects you embark on with this information. Thank you for reading this far.